Introducing Chainless Apps: Bringing Web2 Performance to Web3 Trust at Internet Scale

Today marks a significant leap forward in decentralized application development with the introduction of Chainless Apps. This groundbreaking new paradigm is meticulously designed to combine the unparalleled performance and user experience of Web2 systems with the robust trust and decentralization guarantees inherent to Web3.
The Persistent Web3 Conundrum: UX vs. Trust
For too long, modern blockchain applications have grappled with a fundamental trade-off between user experience and trust. Users often face significant friction managing wallets, incurring gas fees, and navigating complex bridge barriers — obstacles that inherently degrade the seamlessness expected in modern digital interactions. Meanwhile, traditional blockchains, while ensuring strong trust through global re-execution of every transaction, are inherently limited in scalability. Adding decentralization bolsters security and transparency but not throughput, as all nodes perform identical work. This creates a palpable UX gap that decentralized applications (dApps) have historically struggled to overcome. Chainless Apps are designed to bridge this gap, unlocking a new class of user-facing applications previously deemed infeasible under traditional blockchain constraints, such as real-time trading engines, fast-paced multiplayer games, or socially interactive experiences that demand responsiveness, privacy, and verifiability without incurring the latency or UX friction of on-chain interaction.
The Modular Revolution: Decoupling for Performance and Trust
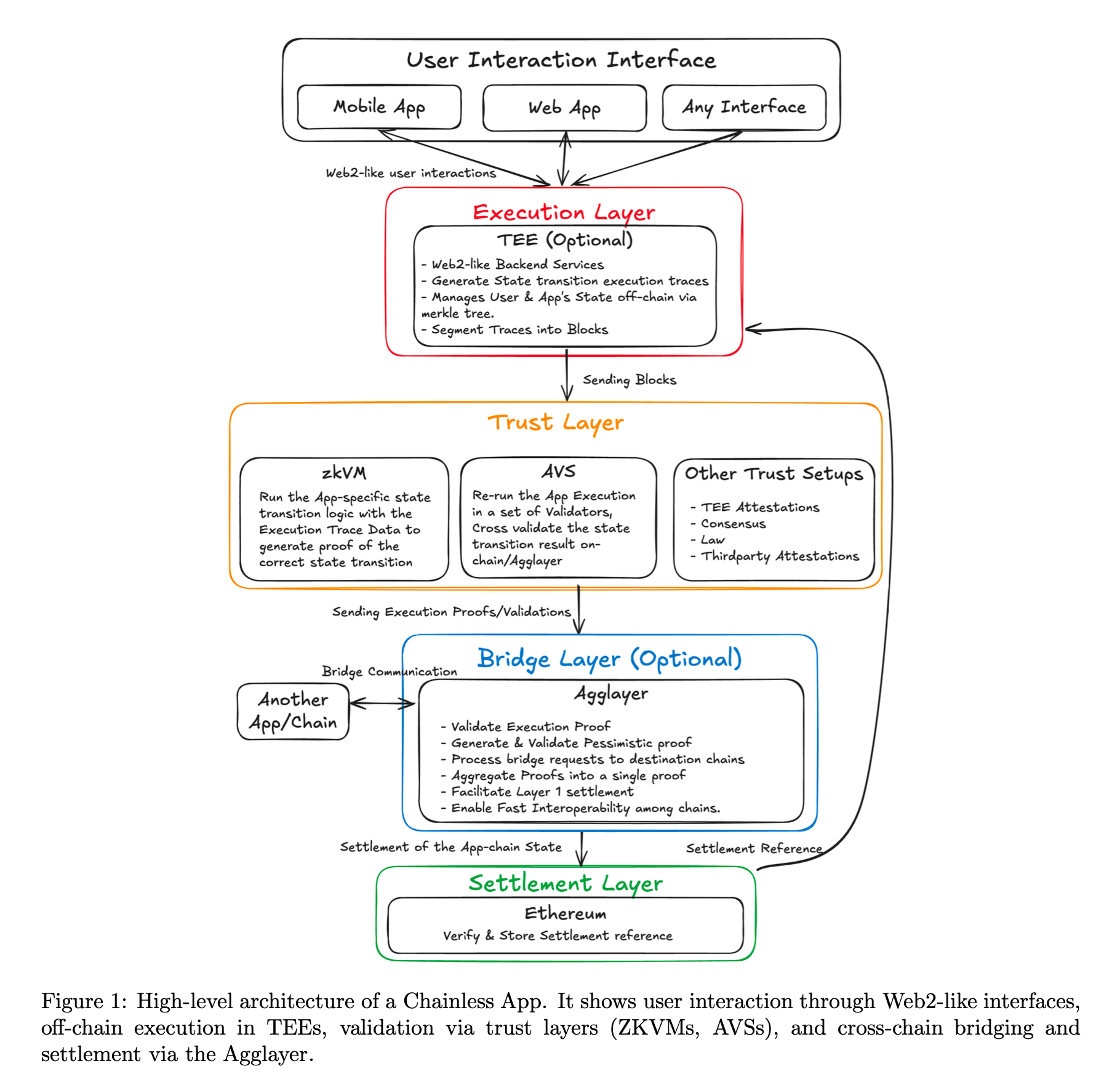
At its core, Chainless Apps redefine application architecture by intelligently separating execution, trust, bridging, and settlement into distinct, composable layers. This modular approach is key to achieving both speed and verifiable trust:
- Execution Layer: This layer is analogous to the backend of a traditional web app, responsible for running the application's core logic and maintaining its off-chain state.
- Crucially, Chainless Apps implement app-specific sequencing: each application defines its own state machine, handles transaction ordering independently, and logs state transitions off-chain.
- This decoupled model delivers significantly higher throughput and responsiveness than global blockchain consensus, enabling thousands of operations per second without being limited by block times or gas costs. Execution can occur in controlled environments like standard runtimes, WASM VMs, or secure enclaves.
- Optionally, execution can even occur inside a Trusted Execution Environment (TEE), such as Intel SGX or AMD SEV, which provides near-native speed and integrity guarantees, protecting internal state from tampering and mitigating Maximal Extractable Value (MEV) by sealing execution order.
- The Execution Layer generates an "execution trace" – an ordered sequence of state transitions committed cryptographically via Merkle roots or hash chains – which serves as the canonical record for later verification.
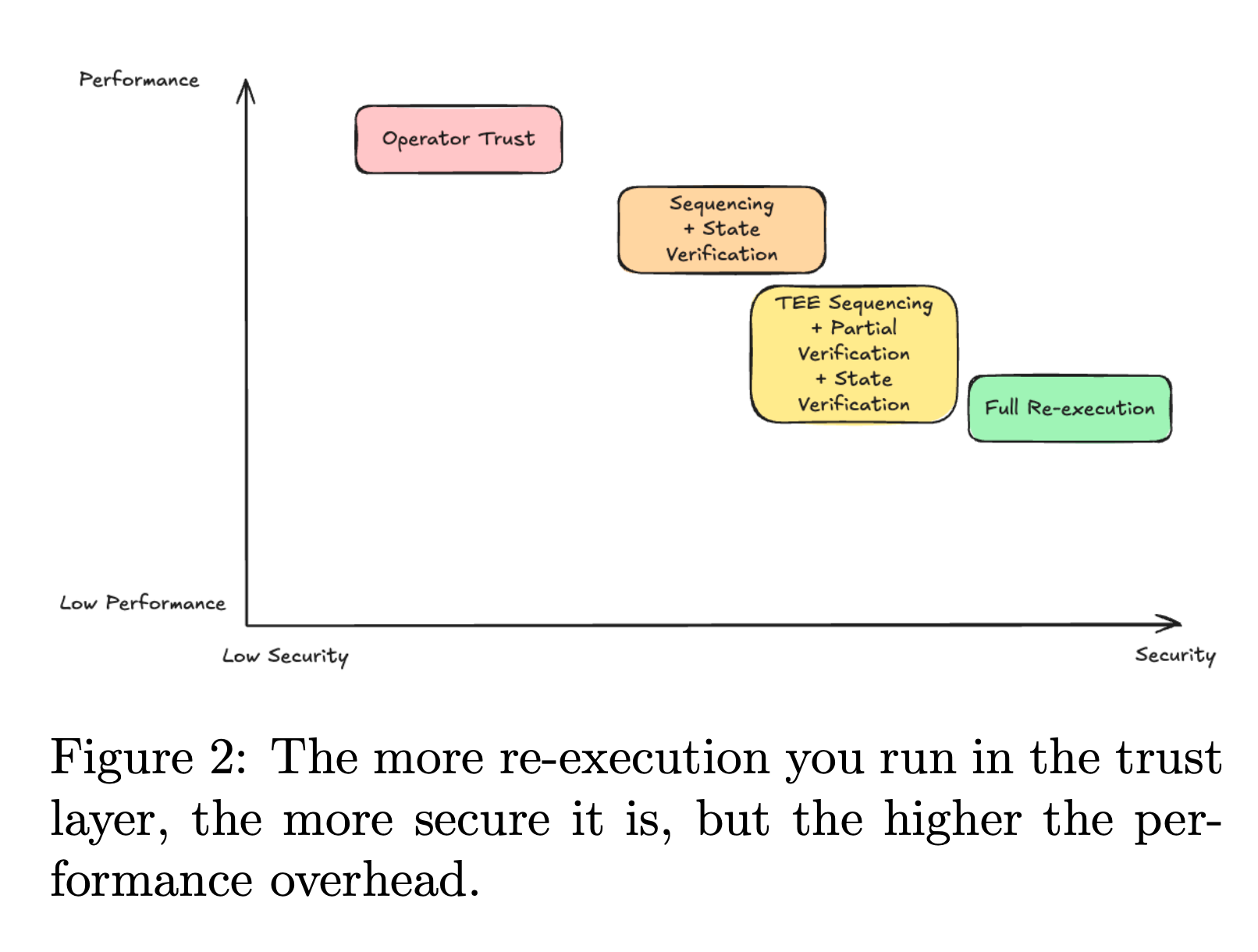
- Trust Layer: This is where verifiability comes to life, providing the crucial trustlessness guarantee by verifying that the Execution Layer's outputs are correct and enforceable. Developers gain unparalleled flexibility in selecting a trust mechanism that best balances their security and performance needs. Options include:
- zkVM Verifiable Compute: This is the most secure approach, utilizing zero-knowledge Virtual Machines (zkVMs) like Plonky3 based zkVMs or RiscZero's zkVM to re-execute the application's execution trace and produce a succinct cryptographic proof (e.g., a SNARK or STARK ) of correctness. These proofs are small (hundreds of bytes) and extremely cheap to verify on-chain, providing strong cryptographic assurances: if the proof verifies, the chance that an invalid computation passed is negligible. This model transforms Chainless Apps into systems akin to validity rollups, where every off-chain computation is independently verifiable.
- Committee-Based Verifiable Compute: Chainless Apps can leverage off-chain validator committees to validate execution traces and ensure correctness. This model, seen in EigenLayer's Autonomous Verifiable Service (AVS) and Truebit, allows for flexible, programmable validation of arbitrary application logic without requiring expensive zk-circuit design upfront, and often provides faster confirmation times. Security typically relies on slashing to deter dishonesty or the assumption of at least one honest participant.
- Operator Trust Compute: At the most trust-dependent end, a Chainless App could operate without cryptographic or game-theoretic verification by simply asking users to trust the operator's off-chain results. This model prioritizes simplicity and speed and might be supplemented with legal contracts or insurance. While not suitable for serious decentralized public-facing apps, it can be acceptable for low-stakes use cases, private betas, early deployments, or institutional developers with other Web2 trust constraints. Importantly, applications can transition from Operator Trust to stronger verification models as they mature.
- Bridge Layer (Agglayer): This is where cross-chain interoperability is seamlessly handled. The Agglayer provides the infrastructure for chain abstraction, unifying liquidity, users, and state across diverse blockchain networks by treating multiple networks as a single, coherent system. This fundamentally solves the fragmentation of cross-chain interaction that plagues Web3, where users traditionally need to manage custom bridges, trust different networks, and risk security breaches. Key features include:
- Unified Bridge: A standardized interface and communication protocol deployed on all Agglayer-connected chains, eliminating the need for chain-specific wrapping or custom bridges and simplifying liquidity flows.
- Pessimistic Proofs: A real-time token balance check that ensures no chain can withdraw more assets than it originally deposited. This mechanism acts as a built-in safeguard against exploits, maintaining liquidity safety across the system.
- Proof Aggregation (Coming Soon): Instead of each chain posting its validity proof to Ethereum individually, Agglayer bundles multiple proofs into one aggregate submission. This significantly reduces settlement costs, improves efficiency, and synchronizes finality across chains.
- Fast Interop (Coming Soon): For real-time use cases, Agglayer will support sub-second messaging across chains, as well as third-party shared sequencing, enabling cross-domain coordination. This allows apps to trigger logic or finalize state on other networks almost instantly, unlocking responsive, multi-chain use cases such as trading, gaming, and composable DeFi.
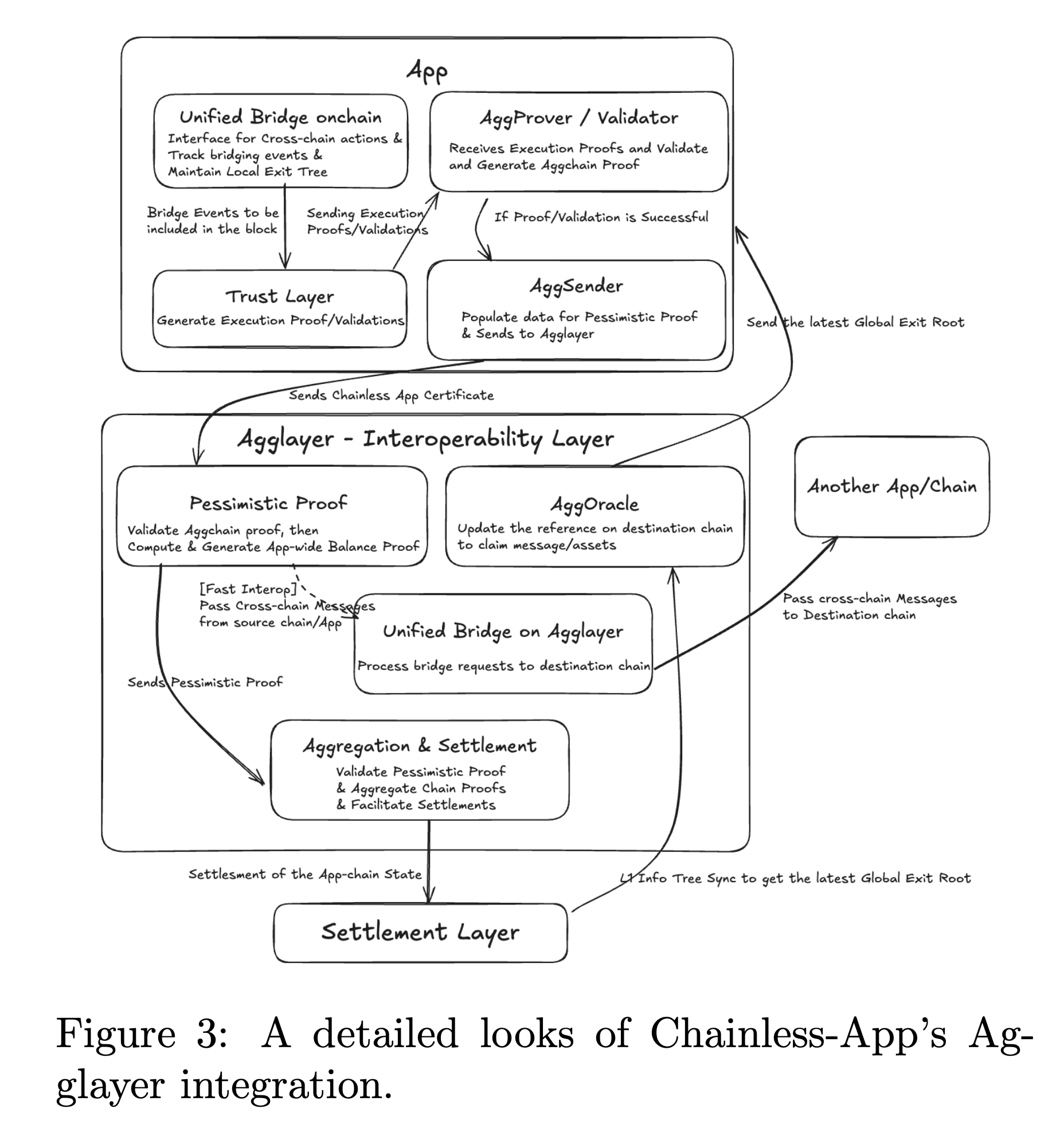
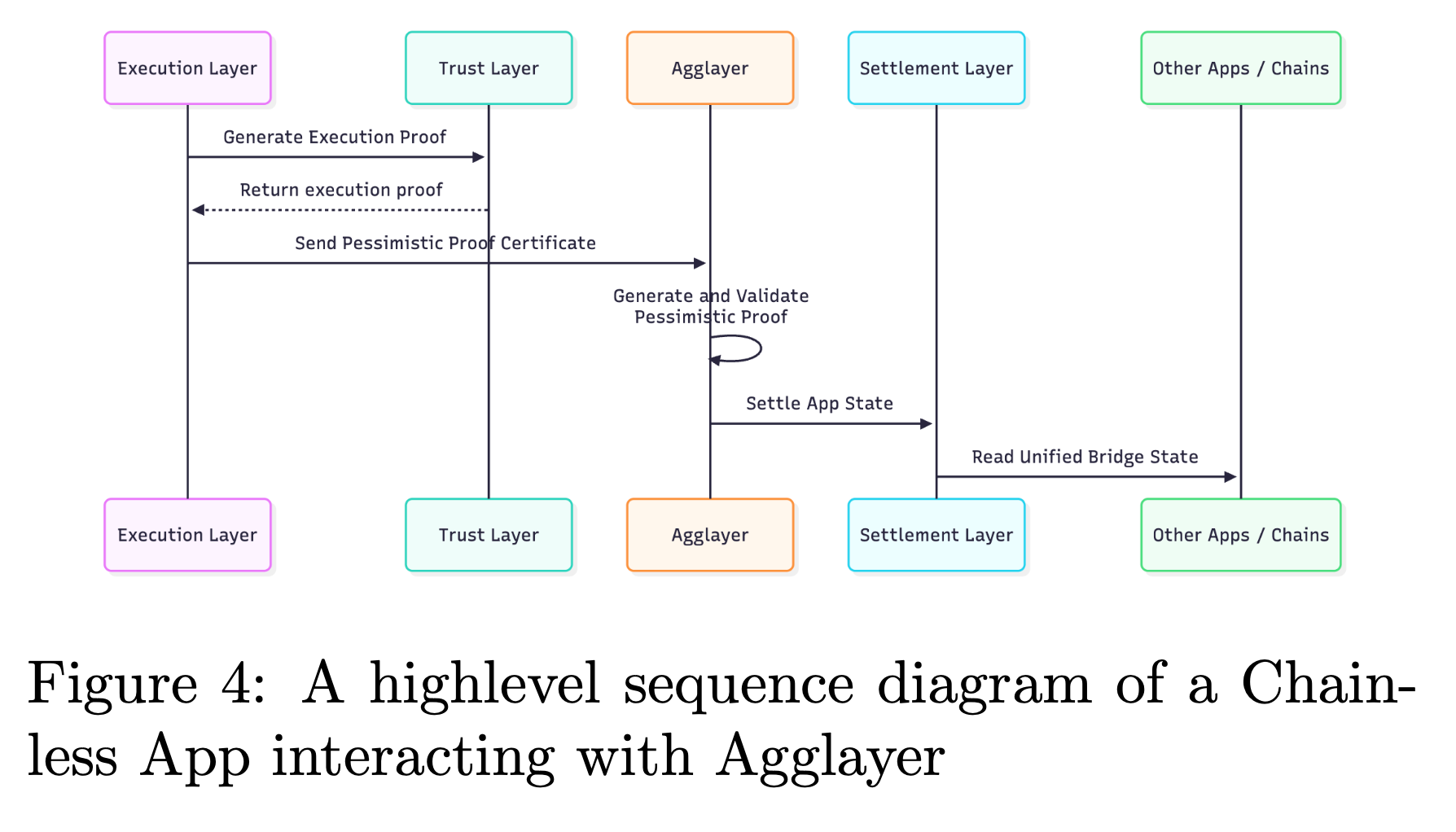
- Settlement Layer: This final step anchors off-chain execution and trust proofs onto a secure base blockchain, typically Ethereum. The Settlement Layer records the final application state immutably on-chain, ensuring full finality, dispute resolution, and long-term security. When the Trust Layer generates a proof (zk proof, validator signatures, or optimistic validation), an Agglayer node submits this data to the Settlement Layer. Along with state roots, bridge events are also recorded to ensure liquidity invariants are preserved across chains. The Settlement Layer acts as the ultimate source of truth: once a state update is finalized, users can safely bridge out assets, reference balances, or resolve disputes based on the canonical on-chain state.
zkSpot: A Glimpse into the Chainless Future
To illustrate the power of Chainless Apps in practice, we've introduced zkSpot, a proof-of-concept high-performance spot trading application. zkSpot aims to deliver the speed and user experience of a centralized exchange (CEX) – with fast order matching, real-time updates, and no visible gas fees – while retaining the trustlessness and self-custody of a decentralized exchange (DEX). Our motto: "Use it like a CEX, trust it like a DEX".
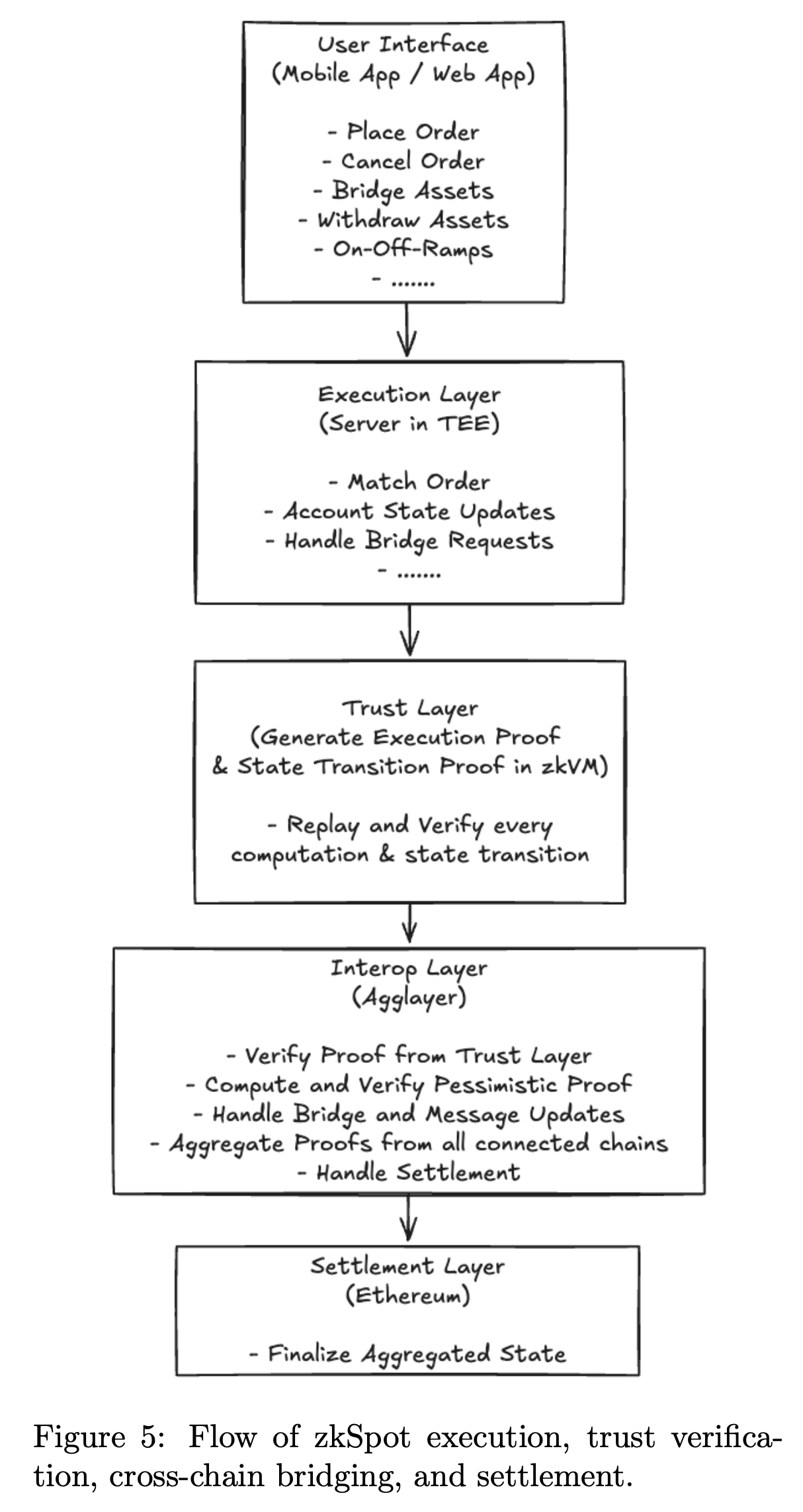
The zkSpot architecture exemplifies a high-trust Chainless App model. Traders interact through a Web2-style web application, able to place orders, deposit assets, and manage balances without signing blockchain transactions in real-time. The Execution Layer runs the trading engine inside a Trusted Execution Environment (TEE), maintaining an off-chain central limit order book (CLOB) where trades are matched and balances updated within milliseconds. The Trust Layer then verifies each batch using a zkVM (such as Succinct's SP1 ) to deterministically replay the trade logic and generate a succinct zk-proof of correctness. These proofs are validated by Agglayer, which then facilitates settlement on Ethereum, immutably anchoring the updated state roots and balance proofs.
Unlocking New Application Frontiers
Beyond trading, Chainless Apps unlock a new class of user-facing applications previously constrained by traditional blockchain limitations:
- 💡 Real-time trading engines: As demonstrated by zkSpot, enabling CEX-like speed with Web3-grade verifiability.
- 💡 Fast-paced multiplayer games: Game logic runs off-chain in native runtimes, with a zkVM verifying actions and enforcing fairness without requiring all logic on-chain. Agglayer interoperability allows NFT rewards or state syncs across chains, creating real-time and cryptographically verifiable gaming experiences.
- 💡 Socially interactive experiences: Providing responsiveness, privacy, and verifiability without incurring the latency or UX friction of on-chain interaction.
- 💡 Private institutional finance systems: Banks or regulated institutions can deploy private Chainless Apps to manage internal processes like payments or compliance checks. The Execution Layer runs business logic in a secure enclave (TEE), with trust enforced through internal attestations, audit logs, or selectively applied zk proofs. Finalized states or aggregate proofs can be posted on-chain via Agglayer for regulatory settlement, unlocking permissioned systems with auditability, verifiability, and interoperability without a full blockchain stack.
- 💡 Verifiable Web2 integration via zkTLS: A Chainless App can securely ingest data from HTTPS APIs (e.g., price feeds, off-chain identities) using zkTLS. The Execution Layer captures a server's signed response over a TLS connection, and the Trust Layer generates a zero-knowledge proof that this response was delivered over a valid TLS session, without revealing full content. This unlocks verifiable oracles and Web2-Web3 bridges operating without trusted intermediaries.
This framework generalizes ideas previously explored in the [A-Z]app Paradigm and aligns with the broader trend toward app-specific design patterns seen in recent systems like #vApps from @LayerZero_Core. Chainless is a multi-stack path into Agglayer; while Polygon CDK powers OP-Geth & Erigon rollups, Chainless powers apps.
Conclusion and Roadmap
Chainless Apps represent a fundamental step towards realizing the vision of a seamless, verifiable, and user-centric Web3 ecosystem. By providing a modular, scalable, and interoperable framework, we empower developers to build the next generation of decentralized applications without compromise. The Chainless App framework has broad applicability beyond trading into gaming, social platforms, data availability, and more, offering a new foundation for scalable, trust-minimized, and interoperable blockchain applications.
Learn more about Chainless Apps and dive into the technical details in our comprehensive paper: https://arxiv.org/abs/2505.22989
We are actively working on development and look forward to sharing further SDK announcements in the upcoming months, enabling developers to easily integrate Chainless App functionality. Stay tuned!

![The [A-Z]app Paradigm - Trustless Apps with Web2 UX and Web3 Verifiability](/content/images/size/w600/2025/04/Blog-Banner--2-.png)
